GPG is a general-purpose encryption system. It can be applied to any file or directory. Given a short walk-through, users should be able to brainstorm new use cases for themselves.
Conceptual Prerequisites
The previous guide introduced the GPG public key system for signing and encrypting email messages. Foundational concepts, such as what does it mean to sign an email and what sorts of guarantees does encryption provide, were discussed at the beginning of that guide. If you haven’t completed the first guide yet, please complete its GPG email tutorial first. See the introductory guide for an overview of how public key encryption differs from a traditional password system.
The only additional requirement to complete it is a basic email client, like Apple Mail, which comes pre-installed on any modern MacOS system.
Technical Prerequisites
- Apple MacOS Catalina, version 10.15.7 or higher
- GPG Suite, version 2022.1 or higher
Use Cases
- Encrypt sensitive information that will be stored on a cloud service, a remote server, or any other environment where access rights are not guaranteed.
- Back up any important information to a local computer in a secure manner. For example, a spreadsheet backup of passwords exported from a password manager.
- Secure personal directories or filesystems on a shared computer by encrypting all contents.
- Sign the contents of a file to verify that it came from you and has not been altered, before sending it on to a recipient or uploading it to a public server. New releases of open-source software often come with a signature for this reason.
Background
GPG tools can be used to sign and encrypt a single file, or an entire directory. If you encrypt a directory, GPG Suite’s default behavior is to place the directory in a .zip file, which you will need to unzip in order to access the files. You can also select any number of files within a directory, and the GPG tools will automatically zip them up into a directory with a generic name (“archive”)
Standard Document Workflow for Signing and Encryption
GPG’s heavy integration into the Apple ecosystem makes the encryption-decryption process very straightforward.
Consider this sample directory in which the user wants to encrypt of spreadsheet-based backup of a password manager program in the file ‘sample-sheet.xlsx’:
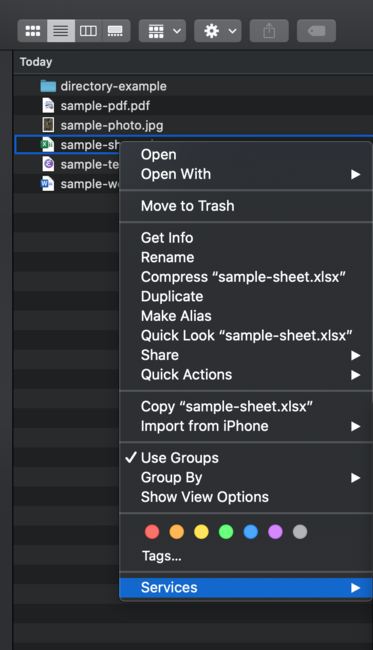
Right click on the file to bring up a menu of file actions, and find “Services,” usually listed near the menu bottom:
If GPG suite is installed and your credentials are stored in the MacOS keychain, you should see a list of GPG Suite actions grouped together, including “OpenPGP - Encrypt File”
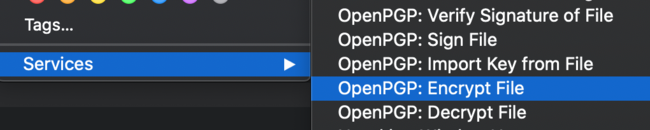
Select this option, and the GPG Keychain should launch.
Recall that PGP encryption of any file (email, a document, etc.) requires you to use a public key. The person who wants to decrypt the file must use the corresponding private key to retrieve it.
GPG prompts you to select the identity of the public key you will use for the encryption operation. This is also known as the “recipient,” or the person who is intended to encrypt the file. This could be any contact whose public key is in your keychain. For this exercise, you can use one of the sample keys you have already created.
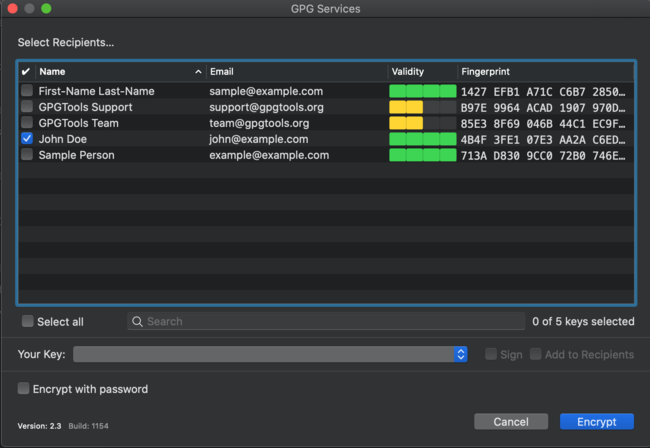
You will also be prompted to select “Your Key”(bottom of screen). By default, GPG Suite will sign the file using whichever key you select.
It is also possible to select multiple recipients. If you check more than one identity from the recipient box, as illustrated below, then any recipient’s private key will be capable of unlocking the documents.
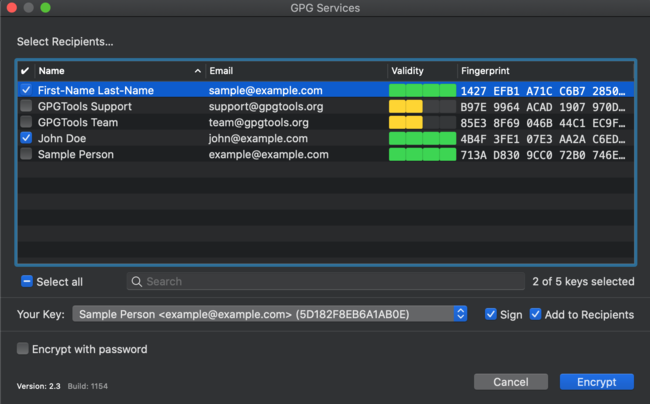
When encrypting, be sure as well to add yourself to the documents. If you only make another person, whose private key you do not possess, the recipient, you will not be able to unlock the documents.
If, as in this example, you intend to encrypt a personal document like a backup of your passwords, and want to designate only yourself as the recipient, keep in mind that anyone who can access your computer and unlock your public keys will be able to use them to decrypt your files. For now we will assume that your keys are secured, and that any private keys you need to decrypt personal documents are accessible only to you.
That’s it! Encrypting ordinary files is even more straightforward than using the GPG system for emails.